Trezor Suite: A Complete Beginner-to-Pro Guide
Master secure crypto management through the official Trezor Suite interface — built for simplicity, powered by hardware-grade security.
Trezor Suite has emerged as one of the most reliable, security-focused crypto management platforms available today. Designed to complement Trezor hardware wallets, this powerful interface allows users to send, receive, exchange, and monitor digital assets without exposing sensitive private keys to the digital world.
Unlike cloud-based wallets or browser extensions, Trezor Suite combines offline private key storage with user-friendly portfolio tools, offering a perfect balance between security and convenience. It caters to both newcomers learning how to store Bitcoin for the first time and long-time crypto enthusiasts managing diverse portfolios.
In this comprehensive guide, we’ll explore everything—from how the Suite works to its top features, privacy benefits, security architecture, and step-by-step usage. If you’re ready to take control of your digital assets, Trezor Suite is one of the strongest environments you can choose.
Unlike cloud-based wallets or browser extensions, Trezor Suite combines offline private key storage with user-friendly portfolio tools, offering a perfect balance between security and convenience. It caters to both newcomers learning how to store Bitcoin for the first time and long-time crypto enthusiasts managing diverse portfolios.
In this comprehensive guide, we’ll explore everything—from how the Suite works to its top features, privacy benefits, security architecture, and step-by-step usage. If you’re ready to take control of your digital assets, Trezor Suite is one of the strongest environments you can choose.
What Exactly Is Trezor Suite?
Trezor Suite is the official software interface for Trezor hardware wallets, enabling secure crypto management across desktop environments. This Suite functions as a “command center” where you can manage accounts, track balances, review transactions, exchange tokens, enable privacy settings, and secure access through your hardware wallet.
What sets it apart is that private keys never leave your Trezor device. Instead, the Suite communicates with your hardware wallet to process and broadcast transactions while leaving all sensitive cryptographic operations offline.
This architecture makes Trezor Suite one of the safest ecosystems in crypto, maintaining complete user control while reducing attack vectors common in hot wallets and browser plugins.
What sets it apart is that private keys never leave your Trezor device. Instead, the Suite communicates with your hardware wallet to process and broadcast transactions while leaving all sensitive cryptographic operations offline.
This architecture makes Trezor Suite one of the safest ecosystems in crypto, maintaining complete user control while reducing attack vectors common in hot wallets and browser plugins.
Top Advantages of Trezor Suite
✔ Secure offline signing through hardware wallet
✔ Fully open-source, community-verifiable codebase
✔ Built-in tools for portfolio management and trading
✔ Privacy mode with Tor routing support
✔ Clean interface suitable for absolute beginners
✔ Fully open-source, community-verifiable codebase
✔ Built-in tools for portfolio management and trading
✔ Privacy mode with Tor routing support
✔ Clean interface suitable for absolute beginners
How Trezor Suite Works
When you open Trezor Suite, it detects your Trezor hardware wallet and creates a secure communication channel. The Suite allows you to view balances and initiate transactions, but the signing—the part that requires your private key—happens inside your hardware wallet.
Even if your computer is infected with malware, attackers cannot access your private keys or confirm unauthorized transactions, as every action requires manual confirmation on your physical Trezor device.
Put simply:
Even if your computer is infected with malware, attackers cannot access your private keys or confirm unauthorized transactions, as every action requires manual confirmation on your physical Trezor device.
Put simply:
Trezor Suite = Visual dashboard
Trezor hardware wallet = Secure transaction signing
Trezor hardware wallet = Secure transaction signing
Trezor Suite vs Software Wallets
| Area | Trezor Suite | Typical Hot Wallet |
|---|---|---|
| Private Keys | Stored offline, never exposed | Stored online/on-device |
| Security Risks | Extremely low | Moderate to high |
| Open-Source Code | 100% open | Varies widely |
| Phishing Protection | Device-level verification | Software-based only |
Key Features You’ll Use Daily
1. Clean & Real-Time Portfolio Overview
Track your crypto holdings across multiple accounts with detailed charts, price data, and transaction history. Perfect for investors keeping an eye on portfolio growth.
Track your crypto holdings across multiple accounts with detailed charts, price data, and transaction history. Perfect for investors keeping an eye on portfolio growth.
2. Built-In Exchange Tools
Buy, sell, or swap cryptocurrencies through trusted third-party providers integrated directly inside the Suite—without exposing private keys.
Buy, sell, or swap cryptocurrencies through trusted third-party providers integrated directly inside the Suite—without exposing private keys.
3. Tor-Powered Privacy Mode
Enable Tor routing in one click to mask your IP address and maximize anonymity during blockchain interactions.
Enable Tor routing in one click to mask your IP address and maximize anonymity during blockchain interactions.
4. Multi-Account Organization
Create separate accounts for different assets, strategies, or purposes, such as long-term storage, DeFi activities, or day-to-day transfers.
Create separate accounts for different assets, strategies, or purposes, such as long-term storage, DeFi activities, or day-to-day transfers.
5. Hardware-Based Authentication
Every transaction requires physical confirmation on your Trezor device, securing your assets even if your computer is compromised.
Every transaction requires physical confirmation on your Trezor device, securing your assets even if your computer is compromised.
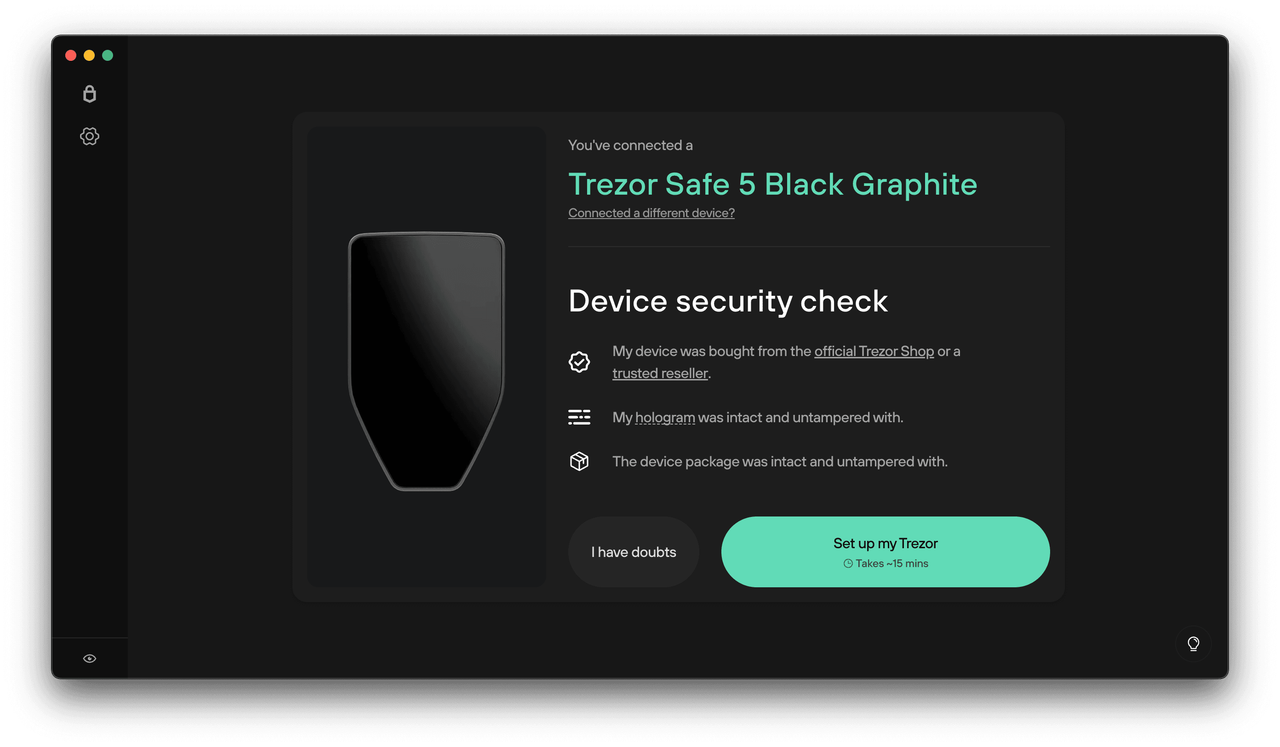
How to Start Using Trezor Suite
Step 1: Plug In Your Trezor
Connect your Trezor hardware wallet via USB. The Suite will detect it automatically.
Step 2: Unlock Your Device
Enter your PIN on the Trezor device screen to unlock and authenticate access.
Step 3: Explore the Dashboard
View accounts, add new wallets, track balances, and customize privacy settings.
Step 4: Send or Receive Crypto
Use verified addresses and confirm actions physically on your Trezor for maximum security.
“The strength of Trezor Suite comes from its unique blend of transparency, hardware isolation, and user-first design — the ideal balance for true crypto ownership.”
Inside the Security Architecture
Trezor Suite relies heavily on secure interactions between software and hardware. Your private keys never touch your computer, browser, or online systems. Each transaction requires:
In contrast to custodial wallets—where funds are controlled by exchanges—Trezor Suite puts ownership squarely in your hands through a transparent, decentralized, self-custody model.
- Verification of transaction details on the Trezor device
- Manual approval via hardware buttons
- Offline signing inside the secure chip
In contrast to custodial wallets—where funds are controlled by exchanges—Trezor Suite puts ownership squarely in your hands through a transparent, decentralized, self-custody model.
Frequently Asked Questions
Is Trezor Suite available for free?
Yes, the application is completely free and open-source for all Trezor users.
Can I use Trezor Suite without a Trezor device?
No. A Trezor hardware wallet is required to access secure functionality.
Does Trezor Suite support Ethereum and ERC-20 tokens?
Yes. You can manage ETH, ERC-20 tokens, and many other supported assets.
What if I lose my hardware wallet?
You can restore your assets using your recovery seed phrase on a new device.
Trezor Suite remains the gold standard for secure crypto management. Whether you're investing in Bitcoin, experimenting with altcoins, or using decentralized finance tools, the Suite offers unmatched transparency and safety thanks to hardware-backed security and a clean, intuitive interface.
By combining offline private key protection with user-friendly portfolio management, Trezor Suite ensures that your digital assets remain entirely under your control—no custodians, no hidden risks, no compromise.
If you’re looking for a reliable, long-term solution for self-custody, Trezor Suite is one of the most secure environments available in the crypto world today.
By combining offline private key protection with user-friendly portfolio management, Trezor Suite ensures that your digital assets remain entirely under your control—no custodians, no hidden risks, no compromise.
If you’re looking for a reliable, long-term solution for self-custody, Trezor Suite is one of the most secure environments available in the crypto world today.